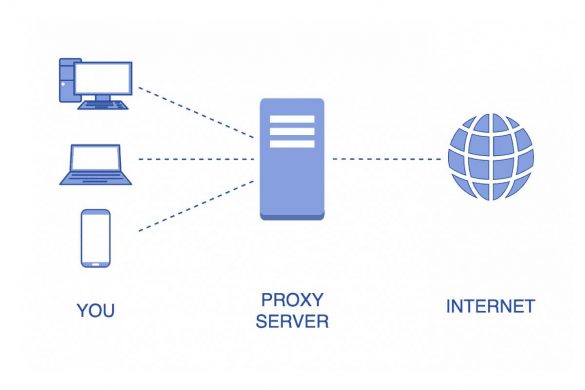
Setting Expectations for a Proxy Service Provider
As with companies in all other sectors, not all proxy service providers are reliable or live up to their promises….
SEO on-page Expert: Tips to Become an Expert
As marketers, we must stay ahead of the seemingly endless updates to the Google algorithm. We run the risk of…
Apex Heirloom
Introduction: Apex Heirloom Relics are Mythic-tier cosmetic items that change the appearance of your melee weapon in Apex Legends. They…
What Are Vector Databases & How Do They Work?
The world as we know it is rapidly changing as new technology is developed for every aspect of modern society….
What is Technology Icon
Introduction ICON Business Support Technology icon Millions of icons are perfect for everything from onboarding flows to presentations and cookbooks….
ASCII Full Form
Introduction: ASCII full form (American Standard Code for Information Interchange) is the most common character encoding format for text data…
Permission Denied Publickey Gssapi With Mic Password
Introduction Permission Denied Publickey Gssapi With Mic Password probably indicates that the SSH private key authentication failed. Assuming you’re using…
Headless commerce: the new way to do business
Headless commerce is a new way of doing business that is becoming increasingly popular. Reading this, someone would be tempted…